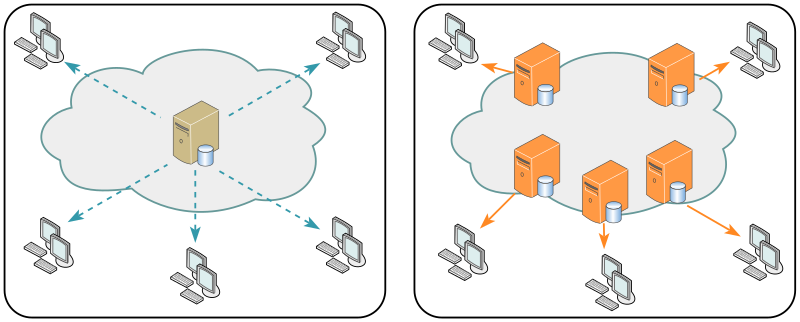
Network topology of the SDN testbed In this research, we deploy TP-Link... | Download Scientific Diagram
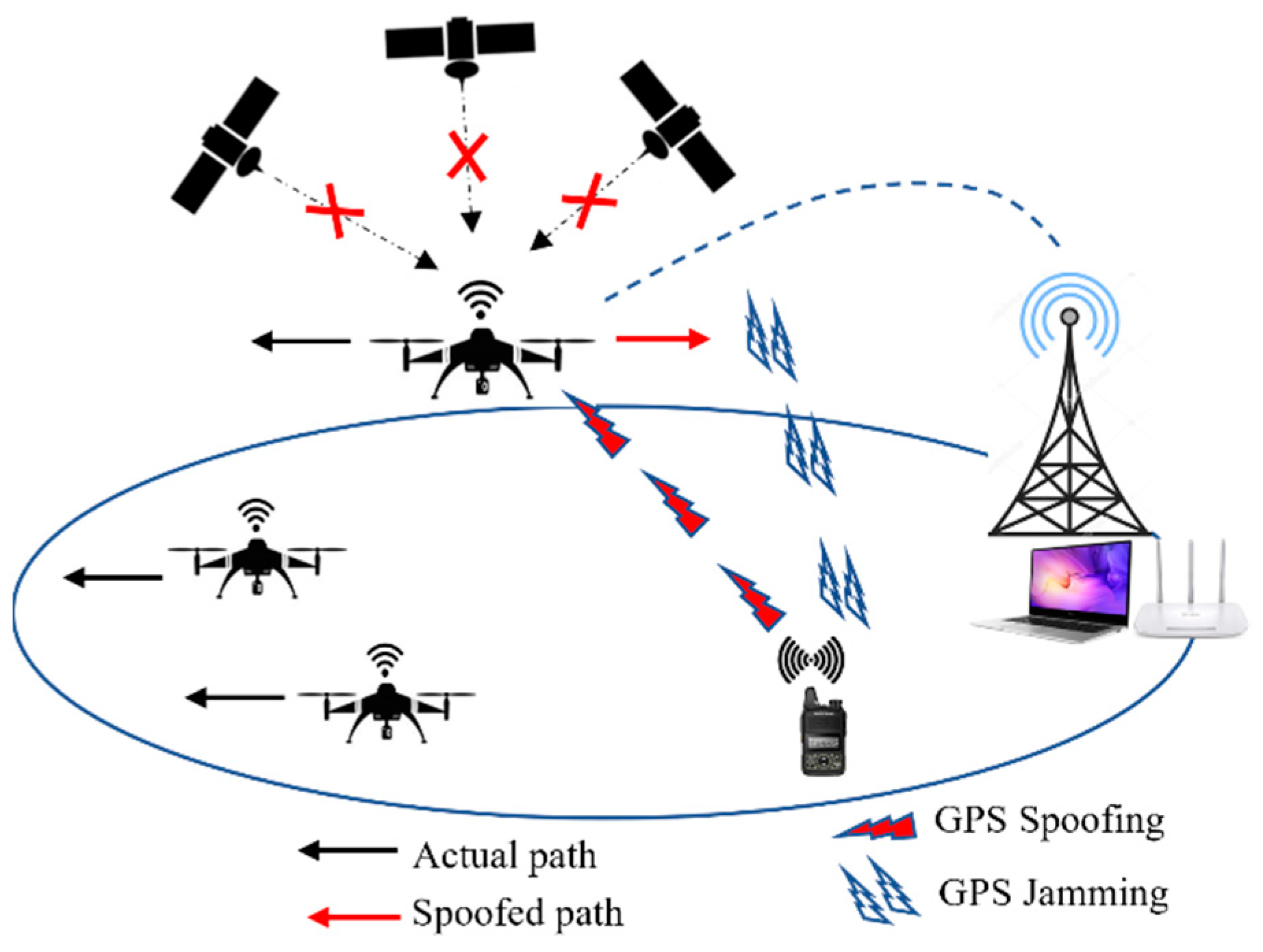
JSAN | Free Full-Text | DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges

New iOS 16 Exploit Enables Cellular Access Under Fake Airplane Mode , Cuba Ransomware Uses Veeam Exploit Against U.S. Organizations, and TP-Link Smart
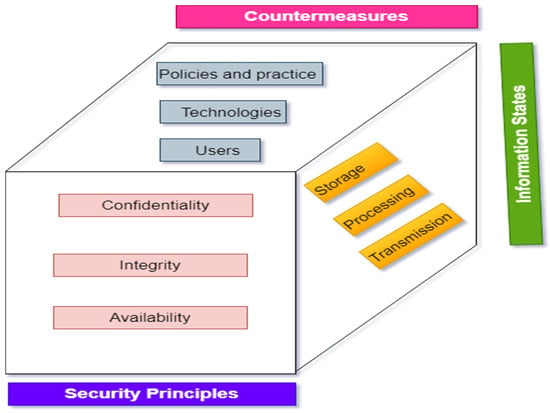
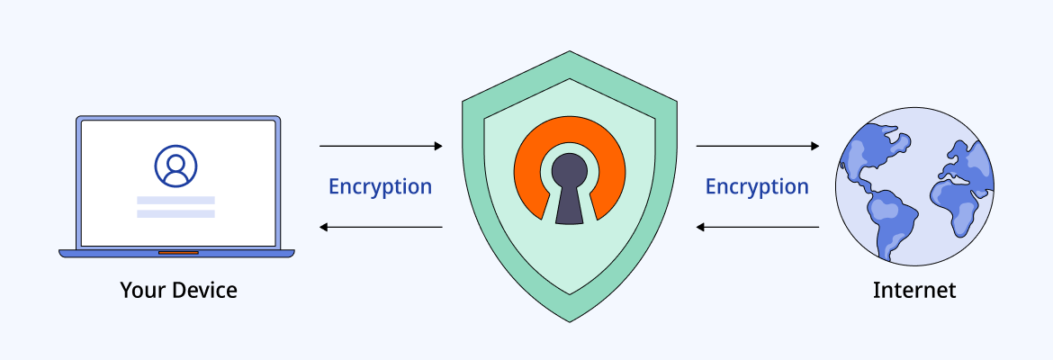
Electronics | Free Full-Text | A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions